When it comes to cybersecurity compliance, words have specific meaning and it is important to get those terms correct. In reality, these cybersecurity documentation terms have quite different implications and those differences should be kept in mind since the use of improper terminology has cascading effects that can negatively impact the internal controls of an organization.
Cybersecurity, IT professionals, privacy and legal professionals routinely abuse the terms “policy” and “standard” as if these words were synonymous, when they are not! ComplianceForge compiled the information on this page to help get everyone on the same sheet of music, since documentation terminology is important as these words have specific meanings as they pertain to cybersecurity and privacy requirements.
Cybersecurity & data protection documentation needs to usable – it cannot just exist in isolation. This means the documentation needs to be written clearly, concisely and in a business-context language that users can understand. By doing so, users will be able to find the information they are looking for and that will lead to cybersecurity and privacy "best practices" being implemented throughout your organization. Additionally, having clearly-written and concise documentation can be “half the battle” when preparing for an audit, since it shows that effort went into the program and key requirements can be easily found.

Click here for a free guide
In simple terms, a policy is a high-level statement of management intent that formally establishes requirements to guide decisions and achieve rational outcomes. A policy is intended to come from the CEO or board of directors that has strategic implications. However, a standard is a formally-established requirement in regard to a process, action or configuration that is meant to be an objective, quantifiable expectation to be met (e.g., 8 character password, change passwords every 90 days, etc.).
In reality, no one should ever ask for an exception to a policy . Exceptions should only be for standards when there is a legitimate business reason or technical limitation that precludes a standard from being followed (e.g., vulnerability scanning exception for a "fragile" application that breaks when scanned by the default scanning profile). It is important that if a standard is granted an exception, there should be a compensating control placed to reduce that increased risk from the lack of the required standard (e.g., segment off the application that cannot be scanned for vulnerabilities).
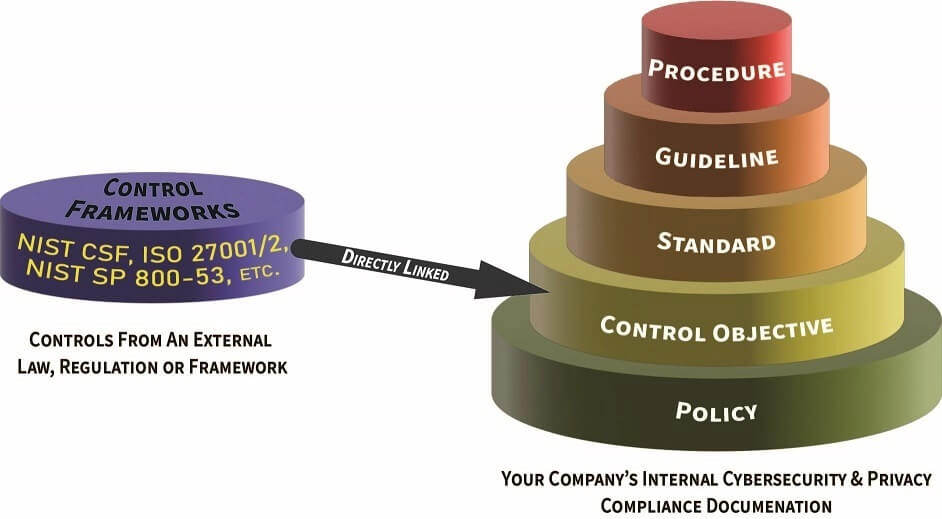
If you visualize these concepts, you can see the hierarchical nature of these documentation components, where policies are the foundation that everything builds upon:
All too often, documentation is not scoped properly, and this leads to the governance function being more of an obstacle as compared to an asset. A multiple-page “policy” document that blends high-level security concepts (e.g., policies), configuration requirements (e.g., standards), and work assignments (e.g., procedures) is an example of poor governance documentation that leads to confusion and inefficiencies across technology, cybersecurity, and privacy operations. Several reasons why this form of documentation is considered poorly-architected documentation include:
In the context of good cybersecurity documentation, components are hierarchical and build on each other to build a strong governance structure that utilizes an integrated approach to managing requirements. Well-designed documentation is generally comprised of six (6) main parts:
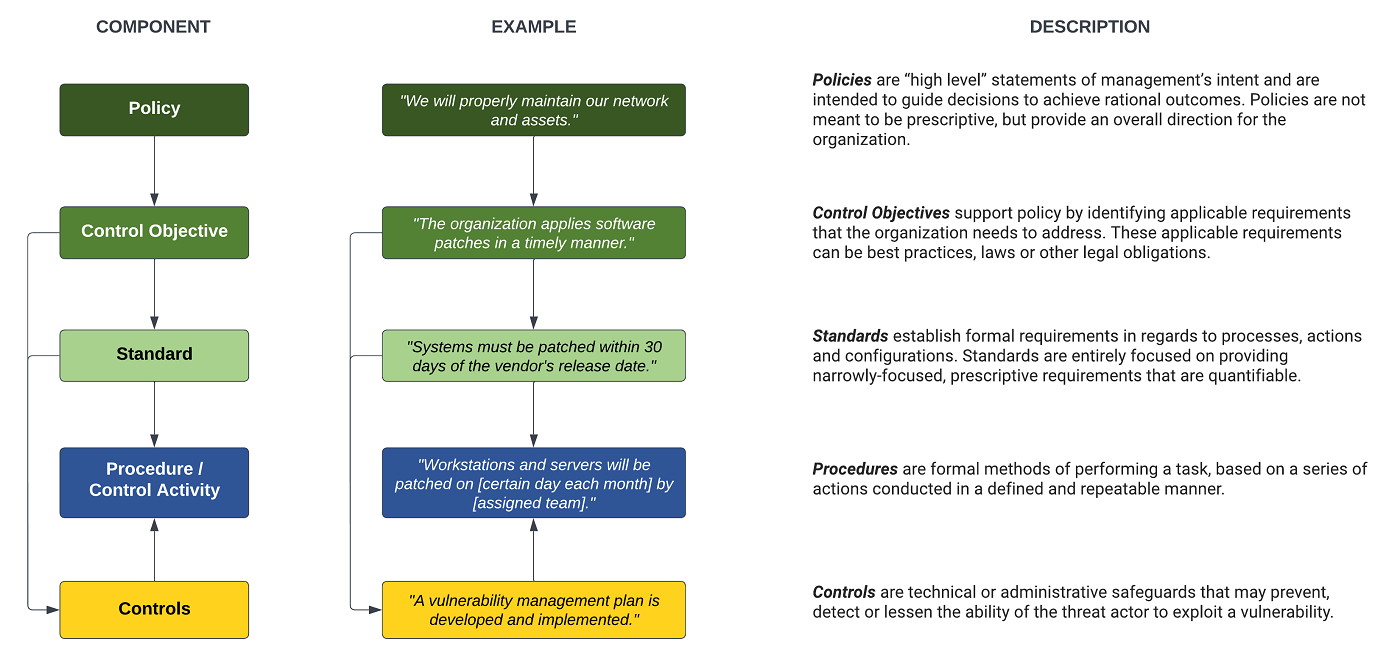
Since words have meanings, it is important to provide examples from industry-recognized sources for the proper use of these terms that make up cybersecurity & privacy documentation:
Policies are high-level statements of management intent from an organization’s executive leadership that are designed to influence decisions and guide the organization to achieve the desired outcomes. Policies are enforced by standards and further implemented by procedures to establish actionable and accountable requirements. Policies are a business decision, not a technical one. Technology determines how policies are implemented. Policies usually exist to satisfy an external requirement (e.g., law, regulation and/or contract).
Control Objectives are targets or desired conditions to be met. These are statements describing what is to be achieved as a result of the organization implementing a control, which is what a Standard is intended to address. Where applicable, Control Objectives are directly linked to an industry-recognized secure practice to align cybersecurity and privacy with accepted practices. The intent is to establish sufficient evidence of due diligence and due care to withstand scrutiny.
Standards are mandatory requirements regarding processes, actions and configurations that are designed to satisfy Control Objectives. Standards are intended to be granular and prescriptive to ensure systems, applications and processes are designed and operated to include appropriate cybersecurity and privacy protections.
Guidelines are recommended practices that are based on industry-recognized secure practices. Guidelines help augment Standards when discretion is permissible. Unlike Standards, Guidelines allow users to apply discretion or leeway in their interpretation, implementation, or use.
Controls are technical, administrative or physical safeguards. Controls are the nexus used to manage risks through preventing, detecting or lessening the ability of a particular threat from negatively impacting business processes. Controls directly map to standards, since control testing is designed to measure specific aspects of how standards are actually implemented.
Assessment Objectives (AOs) are a set of determination statements that express the desired outcome for the assessment of a Control. AOs are the authoritative source of guidance for assessing Controls to generate evidence that can support an assertion that the underlying Control has been satisfied. Generally, all AOs must be satisfied to legitimately conclude a Control is properly implemented.
Procedures are a documented set of steps necessary to perform a specific task or process in conformance with an applicable standard. Procedures help address the question of how the organization actually operationalizes a policy, standard or control. Without documented procedures, there can be defendable evidence of due care practices. Procedures are generally the responsibility of the process owner / asset custodian to build and maintain but are expected to include stakeholder oversight to ensure applicable compliance requirements are addressed. The result of a procedure is intended to satisfy a specific control. Procedures are also commonly referred to as “control activities.”
Risks represents a potential exposure to danger, harm or loss.* Risk is associated with a control deficiency (e.g., If the control fails, what risk(s) is the organization exposed to?). Risk is often calculated by a formula of Threat x Vulnerability x Consequence in an attempt to quantify the potential magnitude of a risk instance occurring. While it is not possible to have a totally risk-free environment, it may be possible to manage risks by avoiding, reducing, transferring, or accepting the risks.
Threats represents a person or thing likely to cause damage or danger. Natural and man-made threats affect control execution (e.g., if the threat materializes, will the control function as expected?). Threats exist in the natural world that can be localized, regional or worldwide (e.g., tornados, earthquakes, solar flares, etc.). Threats can also be manmade (e.g., hacking, riots, theft, terrorism, war, etc.).
Metrics provide a “point in time” view of specific, discrete measurements, unlike trending and analytics that are derived by comparing a baseline of two or more measurements taken over a period of time. Analytics are generated from the analysis of metrics. Analytics are designed to facilitate decision-making, evaluate performance and improve accountability through the collection, analysis and reporting of relevant performance related data. Good metrics are those that are SMART (Specific, Measurable, Attainable, Repeatable, and Time-dependent).
Secure baseline configurations (e.g., hardening standard) are technical in nature and specify the required configuration settings for a defined technology platform. Leading guidance on secure configurations tend to come from (1) Center for Internet Security (CIS) Benchmarks, (2) Defense Information Systems Agency (DISA) Security Technical Implementation Guides (STIGs) and/or (3) Original Equipment Manufacturer (OEM) recommendations.
A POA&M is a “living document” that summarizes control deficiencies from identification through remediation. A POA&M is essentially a risk register that tracks the assignment of remediation efforts to individuals or teams, as well as identifying the tasks and resources necessary to perform the remediation.
A SSP/SSPP is a “living document” that summarizes protection mechanisms for a system or project. It is a documentation method used to capture pertinent information in a condensed manner so that personnel can be quickly educated on the “who, what, when, where, how & why” concepts pertaining to the security of the system or project. A SSP/SSPP is meant to reference an organization’s existing policies, standards and procedures and is not a substitute for that documentation.
In an effort to help clarify this concept, ComplianceForge Hierarchical Cybersecurity Governance Framework™ (HCGF) takes a comprehensive view towards the necessary documentation components that are key to being able to demonstrate evidence of due diligence and due care. This framework addresses the interconnectivity of policies, control objectives, standards, guidelines, controls, risks, procedures & metrics. The Secure Controls Framework (SCF) fits into this model by providing the necessary cybersecurity and privacy controls an organization needs to implement to stay both secure and compliant.
ComplianceForge has simplified the concept of the hierarchical nature of cybersecurity and privacy documentation in the following downloadable diagram to demonstrate the unique nature of these components, as well as the dependencies that exist:
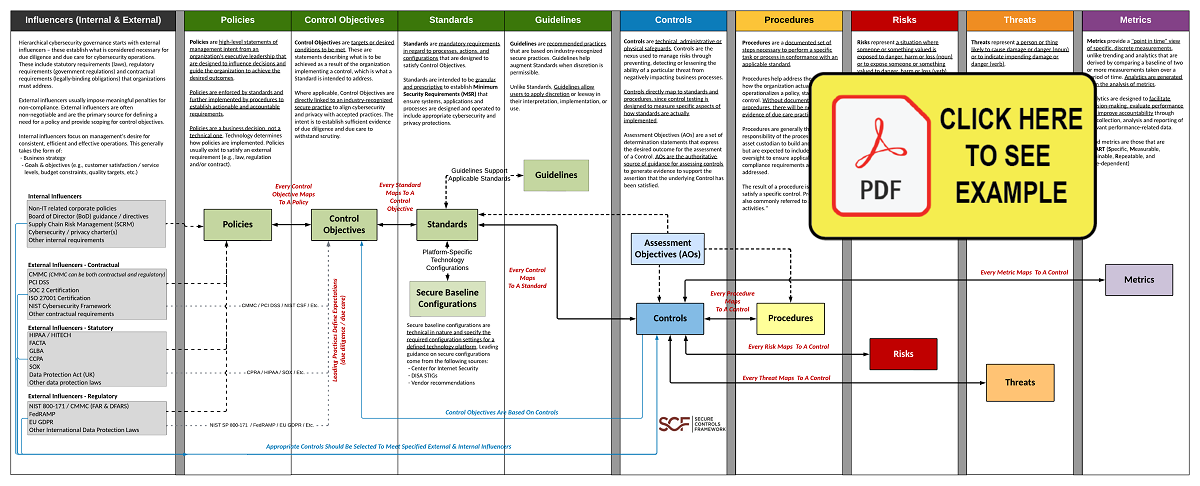
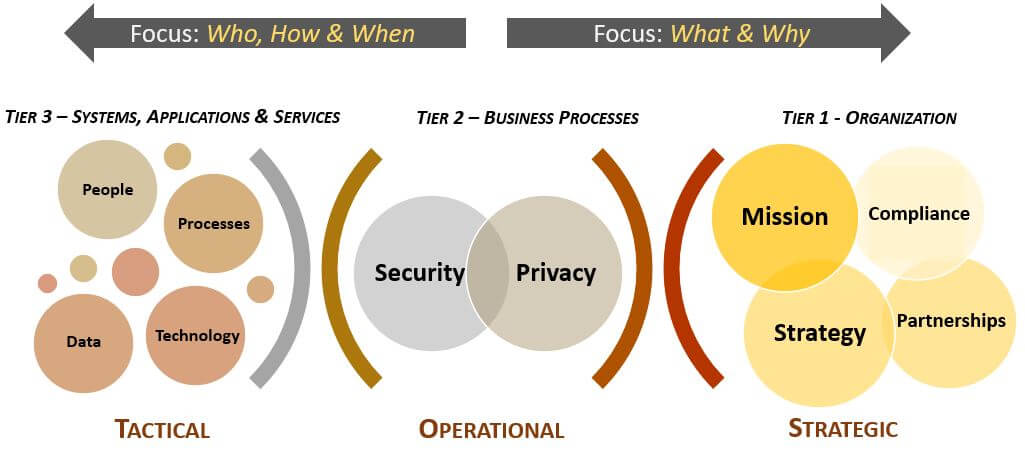
In the context of good cybersecurity & privacy documentation, policies, standards and procedures are key components that are intended to be hierarchical and build on each other to build a strong governance structure that utilizes an integrated approach to managing requirements. Your cybersecurity & data protection documentation is meant to address the “who, what, when, how & why” across the strategic, operational and tactical needs of your organization:
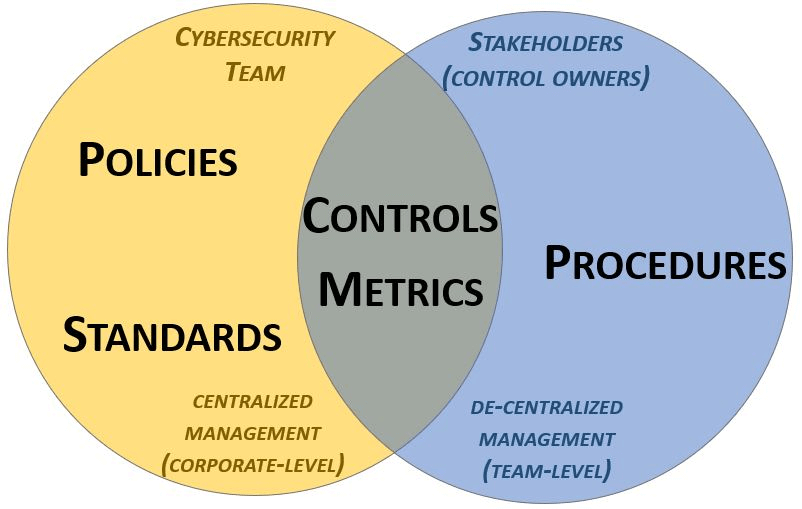
One of the most important things to keep in mind with procedures is that the "ownership" is different than that of policies and standards:
Given this approach to how documentation is structured, based on "ownership" of the documentation components:
Below is an example of how documentation can be broken down from a law/regulation/framework to build documentation (e.g., policies, standards, guidelines, procedures, etc.):
External Framework
Frameworks are often referred to as a standard. In reality, most frameworks are merely a repository of specific controls that are organized by control families (e.g., NIST CSF, ISO 27002, NIST SP 800-171, NIST SP 800-53, etc.).
For example , while NIST SP 800-53 R5 is called a "standard" it is made up of 1,189 controls that are organized into 20 control families (e.g., Access Control (AC), Program Management (PM), etc.). These controls are what make up NIST SP 800-53 as a "framework" that an organization can use as a guide to develop its internal policies and standards that allow it to align with those expected practices.
Internal Security Documentation
An organization is expected to identify a framework that it wants to align its cybersecurity program with, so that its practices follow reasonably-expected controls.
Ideally, there should be a policy that corresponds to each of the control families. This helps make an organization's alignment with its adopted framework more straightforward.
Control objectives provide a 1-1 mapping to address a specific control (e.g., AC-3, AC-7, etc.). For each control objective:
Questions? Please contact us for clarification so that we can help you find the right solution for your cybersecurity and privacy compliance needs.

Secure Controls Framework (SCF) Secure Controls Framework (SCF) "Premium Content" - Expertise-Class Policies, Control Objectives, Standards, Guidelines, Controls & Metrics. Product Walkthrough Video This short product walkthrough video is designed to give a brief overview about.